Code is necessary for electronic gadgets like tablets, computers, and mobile phones to operate correctly. Coding enables communication between these technologies and people. Internal coding systems are used by modern devices, including traffic signals, calculators, smart TVs, and automobiles. Learn everything about Erasure Coding in this article.
Coding serves as a translator since computers cannot communicate in the same way as people. Code converts human input into computer-understandable numerical sequences. Computers that receive these communications perform pre-assigned actions, including centering a picture or altering the font color. Continue reading to discover how code is used to create machines, electronics, and other technologies, as well as to interact with computers.
Erasure Coding: What Is It?
When designing storage systems, IT managers need to think ahead to ensure that mission-critical data is not lost in the event of a failure. Although storage systems exist in a variety of forms, they are all susceptible to malfunction and data loss. Erasure coding is used to avoid data loss in the case of a system failure or natural disaster.
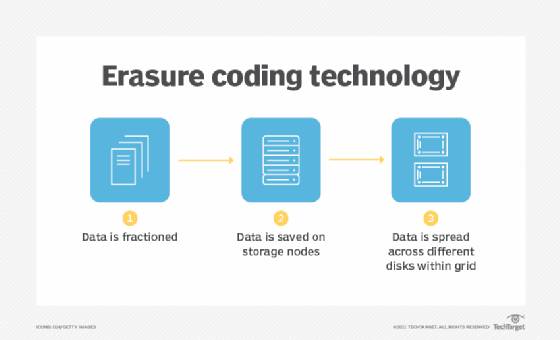
To put it simply, one way to safeguard data is to divide it up into sectors using erasure coding (EC). After that, they are enlarged, encoded, and stored on various storage devices with redundant data pieces. Erasure coding gives the system more redundancy so that it can withstand errors.
How does Erasure Coding operate?
Erasure coding takes original material and encodes it so that, upon retrieval, the original information is recreated using just a fraction of the parts. As an illustration, suppose that the object or data has an initial value of 95. We split it so that x = 9 and y = 5. A set of equations will be produced throughout the encoding procedure.
Let’s say in this scenario it produces equations similar to:
- x plus y equals 14.
- x-y equals 4.
- x + y = 23
Any two of the three equations must be able to be deciphered to reproduce the item. As a result, it is possible to obtain the values for x and y by solving the equations together. Although we have three equations, we can obtain the original data from just two of them. Erasure coding is a data security technique that divides data into pieces, encrypts them, and stores them in many places.
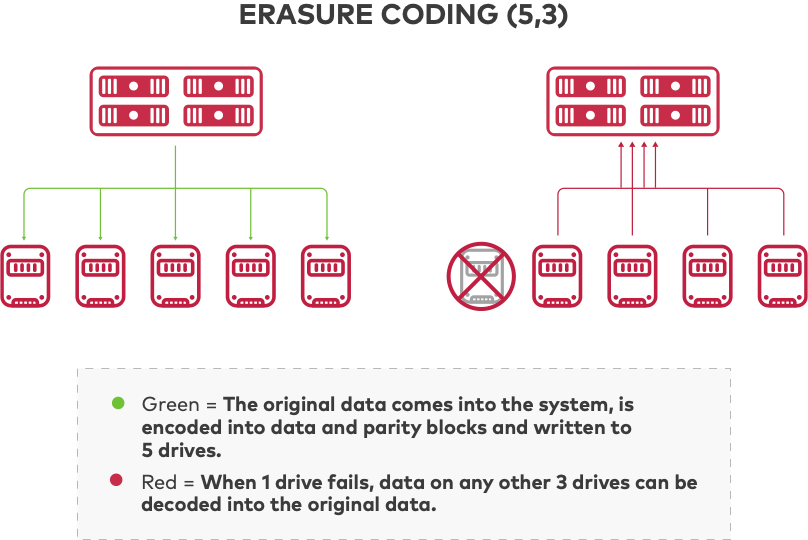
Data Security and Hardware Issues
Due to the frequent occurrence of hardware failure, particularly drive failure, data protection is crucial in any organizational setting. Hardware fault tolerance was traditionally achieved by mirroring and replicating various RAID systems. Replication and mirroring need one or more full redundant copies of the data, which is an expensive method of storage. More sophisticated systems like RAID5 and RAID6, which also reduce storage overhead, offer the same fault tolerance. RAID works well for protecting data on a single node, but it is not scalable since rebuilding failing disks requires time-consuming processes.
For data security, many distributed systems employ 3-way replication, in which the original data is written in its entirety to three separate disks, each of which may read or repair the original data. Replication is not only wasteful when it comes to using storage, but it is also inefficient when it comes to operating after a failure. When a drive fails, the system will switch to a lower-performance read-only mode and fully copy the contents of the failed drive onto a new drive.
Advanced Erasure Coding Techniques or Generally Used Methods:
Successful Interaction:
- Ideas are expressed clearly and straightforwardly.
- To comprehend people, actively listen.
Effective Time Management:
- arranging work in order of priority and urgency.
- establishing reasonable deadlines.
Solving Problems:
- determining a problem’s underlying cause.
- coming up with and assessing possible fixes.
Making Decisions:
- gathering pertinent data.
- weighing the benefits and drawbacks before choosing.
Critical Thought:
- evaluating circumstances impartially.
- challenging presumptions and looking for different viewpoints.
Flexibility:
- Accepting change and gaining knowledge from novel encounters.
- modifying plans in response to changing conditions.
Working together:
- assembling productive teams.
- creating a welcoming and upbeat team atmosphere.
Innovation and Creativity:
- promoting idea development and brainstorming.
- Accepting experimentation and taking measured risks.
Resolving Conflicts:
- proactively and constructively resolving disputes.
- achieving agreements that please everyone.
Ongoing Education:
- keeping abreast of market developments.
- looking for ways to further one’s career.
Establishing Objectives:
- establishing precise, quantifiable goals.
- dividing more ambitious objectives into more manageable chores.
Paying Close Attention to Details
- checking work for correctness in detail.
- looking for mistakes and discrepancies.
Capabilities of Leadership:
- inspiring and encouraging other people.
- efficiently assigning work.
Handling Stress:
- developing constructive coping strategies.
- Make self-care a priority.
Technological Ability:
- keeping up with new developments in tools and technology.
- using technology to make tasks more efficient.
Programming Language Types
A sequence of zeros and ones make up binary code, which is used to transmit instructions. A low-level programming language is used in this code. Your computer has switches that are connected to each digit in a programmed sequence. Thousands of switches work together to run a gadget, with each switch being connected to an action. Programmers may control whole systems at once thanks to high-level code, a kind of computer communication that functions similarly to human language. Programmers use high-level programming languages to translate human language into machine-understandable binary code.
What uses does coding serve?
A range of programming languages are used by developers to create websites and apps. Front-end developers usually generate website layouts and design features using HTML, CSS, or JavaScript code. Computer code that links websites to databases is written by back-end developers for user-accounting websites, such as Facebook, Instagram, and LinkedIn.Python, Java, and SQL are common programming languages used by back-end developers.
Other programming languages like Python, Objective-C, C#, Swift, or Ruby on Rails are used by developers to make computer software and applications for mobile devices. The most popular programming languages and their typical applications are listed below.
C:
- used in the creation of databases and operating systems software
Python:
- used in the development of software, websites, and data analysis
HTML:
- used to create webpage structures such as tables, links, and paragraphs
Rails on Ruby:
- used for doing data analysis and creating applications and web pages
C++:
- used in the development of video games
C#:
- used to create online services and desktop apps
Scala:
- used to help with web development, data processing, and data engineering
Perl:
- used for network programming, web development, and text manipulation
PHP:
- used for dynamic web page creation and database management
SQL:
- utilized for managing and organizing data as well as interacting with databases.
JavaScript:
- used to enable front-end and back-end development and to create webpages
Quick:
- utilized to create applications, mostly for Apple platforms
Goal-C:
- used while creating applications for Apple devices
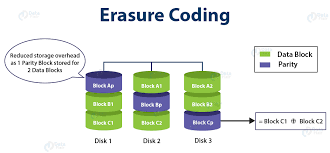
Erasure Coding Versus RAID
Erasure codes were created more than 50 years ago to aid in the detection and correction of data transmission faults. They are sometimes referred to as forward error correction codes. Since then, the technique has been used in storage to help safeguard data against corruption or drive failure. Recently, the usage of EC with huge object-based data sets—especially those stored in the cloud—has grown in popularity. The growing size of data sets and the rising adoption of object storage make EC a more attractive option than RAID.
RAID
RAID uses mirroring and striping with parity to safeguard data. One easy way to secure data is to mirror it. On its alone, it’s RAID 1. In this configuration, data is copied over two or more drives. Data may be restored from another disk without affecting service in the event of one disk failing. Like any replication technique, mirroring is easy to set up and maintain, but it needs a sizable amount of storage capacity. Data is protected by RAID 5 by being stripped over many hard drives and parity blocks added. It is possible to recover a failed disk by using data from other drives. RAID 5 can only tolerate a single disk failure, though. Consequently, some businesses provide RAID 6 storage solutions, which are capable of withstanding two disk failures simultaneously. RAID 10 combines RAID configurations to secure data through disk mirroring and parity-free data striping.
RAID configurations have been a mainstay of data center operations for many years because the technology is well-known and dependable for a range of workloads. Major problems exist with RAID. Striping with parity can only stave off two disk failures concurrently, and mirroring is a waste of resources. Moreover, RAID has capacity problems. Larger disk drives require more time to rebuild in the event of a failure. Data loss may rise and application performance may be slowed as a result. In a RAID 5 configuration, repairing a broken disk might take several days, resulting in an unsecured storage array until the rebuild is finished. Program performance may also be impacted by a disk failure.
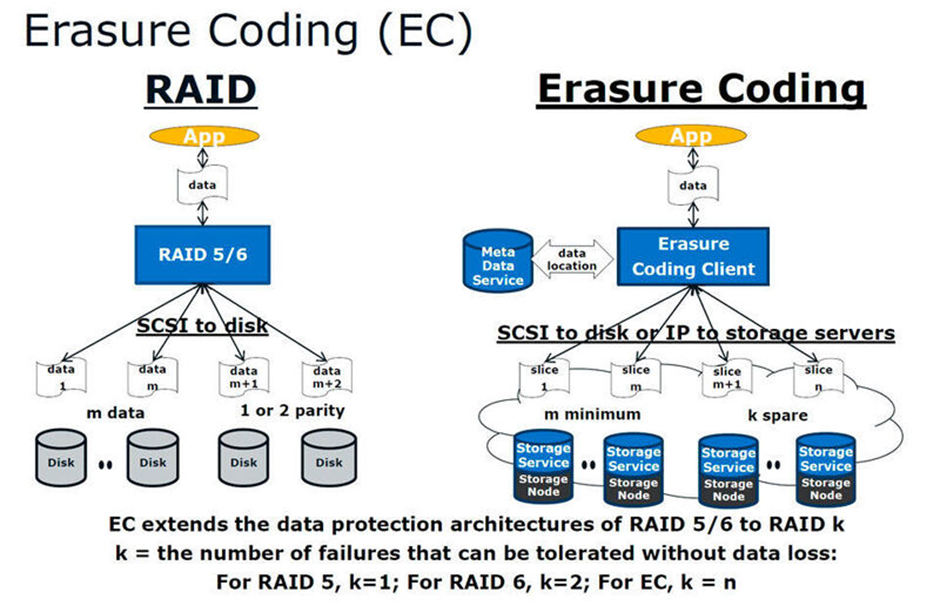
Coding Erasure
RAID can be lessened by using erasure coding in its stead. Erasure coding improves fault tolerance by accepting more failed disks than RAID 6. Spreading 16 data and polarity segments over 16 drives allows a 10+6 erasure coding configuration to withstand six drive failures. Erasure coding is flexible, while RAID configurations are rigid. With EC, organizations may tailor their storage system to their specific data protection requirements. Disk rebuilding can also be accelerated by EC, depending on the parameters and disk count.
EC has a significant disadvantage, notwithstanding its advantages: performance. Erasure coding involves a lot of processing. All drives must have data and parity segments written to them, and all storage data must have the EC algorithm run on them. Rebuild operations put an additional burden on CPU resources since, if a drive fails, data must be restored instantly. When used with parity RAID configurations, mirroring or striping seldom reduces performance and usually improves it.
What uses does erasure coding serve?
Erase coding is a common security measure used by major cloud storage providers such as Amazon S3, Microsoft Azure, and Google Cloud to protect their massive data repositories. Because it safeguards dispersed and object-based storage systems, erasure coding is perfect for cloud storage. Erasure coding is now used in on-premises object storage systems such as Dell EMC Elastic Cloud Storage (ECS). Erasure coding is useful for handling mistakes and massive volumes of data in disk array systems, data grids, object stores, distributed storage applications, and archive storage. For the majority of contemporary use cases requiring large data sets, RAID is not feasible. Since EC needs high-performance infrastructure, large cloud services are its primary application.
For static, non-write-intensive data collections, such as backups and archives, erasure coding is advised. Many applications employ erasure coding to reduce replication costs. EC is used to reduce duplicated data storage costs across data nodes in several Hadoop Distributed File System (HDFS) implementations. For data safety in object storage systems, Hitachi Content Platform now provides erasure coding.
What advantages does erasure coding offer?
While EC provides several significant advantages over RAID, it is still a valuable tool for data security and should be taken into account when organizing data storage.
- Improved use of available resources. RAID 1 mirroring and other replication methods consume a large portion of storage space for data copies. Erasure coding may save a lot of storage while maintaining data security. Depending on the encoding arrangement, the precise amount of capacity saved will vary, but it will still result in increased storage economy and reduced storage expenses.
- Reduced chance of losing data. Rebuilding a broken drive in a RAID array composed of high-capacity disks might take a very long time, increasing the chance of data loss if another drive fails before the first one can be repaired. Depending on the encoding settings, erasure coding can tolerate many more simultaneous disk failures, reducing the likelihood of data loss in the event of a drive failure.
- Increased adaptability. RAID is usually restricted to quiet set-up installations. While proprietary RAID configurations can be implemented by companies, most RAID implementations follow a fairly common protocol. Much greater flexibility is offered by erasure coding. The data-to-parity ratio that best suits an organization’s unique workloads and storage systems can be selected.
- Increased robustness. An organization can set up a storage system with a high level of durability and availability by using erasure coding. Amazon S3, for instance, is engineered to provide 99.999999999% object durability throughout several Availability Zones. An EC-based system may be built to endure far more simultaneous disk failures than RAID 6, which can only withstand two.
Organizations must plan their storage methods taking into account several aspects, such as disaster recovery and data loss prevention. RAID is one method and straightforward replication is another. Another is erasure coding.
There are benefits and drawbacks to any technique. But as data volumes increase and object storage becomes more prevalent, EC will undoubtedly gain traction. Organizations may achieve scalability requirements and maintain data security with erasure coding, all without having to pay the hefty expenses associated with complete replication. Nevertheless, no technology can advance without adjusting to market shifts, and in five years, the EC that is currently in use may look very different.
In summary:
In summary, the complex dance that occurs between people and electronic gadgets depends on the language of code. The function of coding grows more and more important as technology becomes more and more integrated into our daily lives, from little devices like computers and mobile phones to bigger systems like traffic lights and smart TVs. Code functions as a translator, translating human intents into numerical sequences that computers can understand. The smooth operation of machinery, electrical gadgets, and other technology is made possible by this mutually beneficial interaction, which also shapes the environment of our contemporary, networked world.
Questions and Answers (FAQs):
1. Why is coding used in electronic devices?
Coding facilitates communication and gives instructions to electronic equipment, acting as a bridge language between people and machines.
2. How do computers interpret code that comes from human input?
Computers translate human input into numerical sequences by deciphering instructions that are encoded. These patterns direct computers when they do operations like text formatting and picture manipulation.
3. When it comes to IT systems, what does Erasure Coding mean?
IT administrators use erasure coding (EC) as a data protection technique while building storage systems. To prevent data loss in the event of a system failure, it entails dividing data into sectors, expanding and encrypting them with redundant portions, and distributing them over several storage media.
4. Why is data security by erasure coding important?
Erasure Coding gives storage systems redundancy, which makes them more resilient to faults. Data loss can be avoided by using dispersed and encoded data fragments to reconstruct the original information in the case of a system failure or disaster.
5. How is Erasure Coding implemented?
Erasure coding is the process of encoding original data so that, to reconstruct the original information, a small portion of the parts are needed. For instance, the encoding process could split the original data value of 95 into smaller pieces, such as x=9 and y=5, resulting in a set of redundancy equations.
6. Could you give an illustration of the redundancy that Erasure Coding adds?
Yes, take into account a 95 original data value. It might be divided into subsets like x=9 and y=5 using erasure coding. Data integrity is ensured since both of these subsets may be utilized to recover the original information even if one is destroyed or lost.
Also Read How to Learn Coding for Free? Learn Coding for Free










Add Comment